Advanced Computer Forensics
- Prodiscover Basic Edition
- Prodiscover Basic Features
- Prodiscover Basic Download
- Prodiscover Basic Forensics Software
- Prodiscover Basic Free
Windows ProDiscover Forensics Lab
- ProDiscover Basic. ProDiscover Basic is a simple digital forensic investigation tool that has tools for images, analysis, and reports on evidence found on drives. The Sleuth Kit is an open source digital forensics toolkit that can be used to perform in-depth analysis of various file systems. Autopsy is a GUI for The Sleuth Kit.
- This tutorial is for educational purposes only.In this tutorial i will use Prodiscover Basic to create an image of a drive and be able to retrieve all the da.
- Starting ProDiscover Basic On your desktop, double-click the 'ProDiscover Basic' icon. In the 'Launch Dialog' box, enter a 'Project Number' of 15 and a 'Project File Name' of 15-YOURNAME, replacing 'YOURNAME' with your own name, as shown below: Click Open. This creates a Project, but so far the Project has no evidence in it. Adding an Image File.
This lab is a replacement for the EnCase lab (122) for students who have been unable to access EnCase through RLES. In order to do this lab, you will need to download and install ProDiscover Basic (make sure to pick 32-bit or 64-bit depending on your version of Windows) from this URL: http://www.techpathways.com/desktopdefault.aspx?tabindex=8&tabid=14 (scroll down until you see the download links at the bottom of the page). You will also need to download a copy of the image files for this lab, 123img.zip. These image files are distributed under the GPL and were originally created by Brian Carrier.
02 prodiscover basic free download. Office2textile This project provides VBA add-ins which convert Microsoft Office contents to various text formats.
Instructions appear as bullet points, questions are numbered and bolded.
Instructions & Questions
- Start ProDiscover Basic.
- Create a new project for this laboratory. Give it a unique number and name.
- Click “Add” then “Image File” and add “123img1.dd”.
- Click the “Action” menu then generate “OS Info”. This adds some information about the image to the report, which you can view at any time during your examination by clicking on “View” then “Report”.
- What is the file system of this image file?
- What is the volume name?
- Go to “Cluster View” and click on the image.
- How many clusters are used on this image file?
- Go to “Content View” and click on the image.
Prodiscover Basic Edition
- List all the Deleted files recovered by ProDiscover in a table – and calculate the MD5 hash value for each deleted file.
- Is there anything special about any of the files?
- ProDiscover will use the time zone setting of your examiner workstation if no time zone is set for the evidence. When you acquire a computer as evidence it is important to make note of the computer’s time and time zone, especially if you need to correlate evidence from different time zones (never assume the time or time zone on a computer is correct.)
- Where does the Time Zone information reside in a Windows system?
- Set the timezone by clicking on File, then Preferences. The timezone should be US Central Time in this particular case (the image file has been extracted from a computer in that timezone although it is not an image of the system partition so there is no way to find the computer’s actual timezone from the image itself).
- What is the latest file creation time on the image?
- Which files are resident files? Hint: you can right-click on a file and say “Show Cluster Numbers” to see the cluster/s in which the file is stored – you can do this for the $MFT of the disk image to see which clusters are allocated to the $MFT.
- Add the second image to the case – “123img2.dd”
- Go to the “Content View” and click “All Files”.
- Go to the “View” menu and select “Gallery View”.
- Which files display a thumbnail in Gallery View?
- Are there any files with mismatching file extensions? If so, which ones? Identify their types according to their extension versus their actual type and explain how you have identified the actual type.
- Disable Gallery View.
- Extract all JPEG files from the image by selecting each of them. You will be prompted to add a comment about the file for the report. Record “JPEG file” and whether the file has been hidden, deleted, mislabelled or is in any other way special.
- Right-click on a file and click “Copy All Selected Files”. Save them in a temporary directory on your computer.
- Paste each JPEG file from your temporary directory into your submission document as an embedded image.
- Do you think you have identified every JPEG file in the image? Hint: You can search for the JPEG file header by clicking on “Search”, selecting “Hex” and searching for the pattern FFD8. Do any files contain the pattern which do not appear in your temporary directory? If so, which ones?
- Create a table for all files on the second image, listing each file’s name and MD5 hash value.
Your answers to all questions should be stored in a LibreOffice document, Word document or PDF, and uploaded to Dropbox in the “EnCase Lab” folder as this exercise replaces the EnCase lab.
ITC597 Digital Forensics Proof Reading Services
Task 1
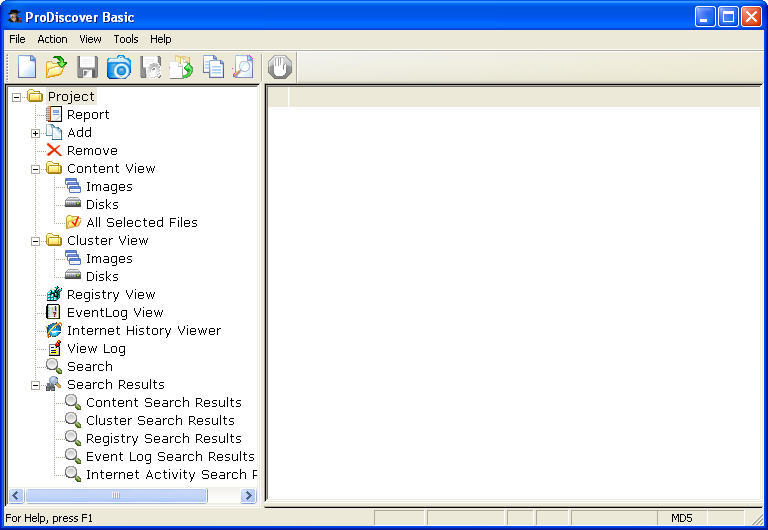
Hands-On Project 1-1
Firstly I have come across many new things while performing these tasks. In the initialisation period I get to know about the case involved in this project. This was a murder case of a girl. The case had been reported by her boyfriend. I learnt how the skilled technicians work at the crime scenes; this was the time the term “ProDiscover” coined in my eyes. By this part of time, my interest towards image analysing tool that is arouses.
1.ProDiscover basic which provides detailed information of the image. This tool is not supported by any MAC, CD-ROM and UNIX which I was unaware of before this. I have learnt that ProDiscover basic supports only NTFS and FAT format. I have learnt allot about the working of ProDiscover basic.
2.I learnt the importance of giving name in specific format to a new project. There are series of step, I learnt. The very first step was to install the software ProDiscover basic and add new project.
3.The very next step was to include the image in your work area.
4.Followed by this step, there was need to select the path of the image file, select the view option to run the associate program.
5.I came to knew that, this software has an extended feature of exporting the individual file. This feature is really helpful when you have to work with individual module of complete project. ProDiscover basic does not provide auto save feature, so there is need of manually saving each project.
6.ProDiscover Basic tool needs to be exit before a new project has been begin which is kind of limitation which I come across so far.
The thing which I deduced with this tool is that ProDiscover basic tool is never recommended as a preliminary forensic tool but within budget constraint this tool is good choice.
Hands-On Project 1-2
Prodiscover Basic Features
I came across so many new concepts which are associated with Forensic examination. The case begins with introduction about the company and what was the issue associated with the company.
My duty was to examine all the forensic examinations and computing internal investigations. I was assigned a duty to examine a USB drive which has been left by a former employee. That employee has been accused for stealing critical information of the company. There are in total 24 files confidential files with text “book”.
There are list of 5 things which I learnt while carrying out the examination of USB drive:
1.Which Tool used: I learnt about the various Images analysing tool. Taking care of the specifications and other things, ProDiscover basic was best among them. The very first step, I learnt the extraction of image file C1PRJ02.eve file to the work area.
2. Opening new project: The process starts by opening a new project and giving a valid name to it, there is need to give brief description about the project. There is no auto save feature provided by ProDiscover basic. There is need to save the project immediately.
3.Adding image file: There is need to add the image file C1PRJ02.eve to your project. This is done from action option in menu and click on add. There is need to check yes for auto image checksum message box.
4.Search toolbar: The preliminary step is to go for a search toolbar to check for a keyword. This will help in
5.Content search methodology: This project helps me to learn how then search processes work in a disk/image file. It is recommended to carry out content search tab and then select the ASCII option and then select the search for the pattern option to search for the keyword ”book”. There is also feature of cluster search while takes a little more time than simple content search.
Hands-On Project 1-3
This case is related to an additional drive which has been used by former employees and may have had access to account number ’461562’ which belongs to vice president of company and may have had access to internet banking.
There are list of 5 things which I learnt while carrying out the examination of external drive:
1.Which Tool used: I learnt about the various Images analysing tool. Taking care of the specifications and other things, ProDiscover basic was best among them. The very first step, I learnt the extraction of image file C1PRJ03.eve file to the work area.
2.ADD the evidence: Add the evidence to the new project. Navigate the image file/drive to the work area and open it. Select yes to auto image checksum. ProDiscover can add .dd image files (standard UNIX).
3.Expanding the content view: I get to learn how to view the graphic files in a drive. Expand the content and select the file path of the image. And click on view from gallery view from the menu. It displays all the graphical files on the drive. Notes can be added to the selected image.
4.Content search tab: Select the content search tab for searching given account number. Then there is need to carry out the cluster search and remember to select the desired result and add comments to it. This helped me to distinguish it from other images.
5.Exporting: while doing this project, I learn how to do export the report. Select the RTF format and type the file name.
Hands-On Project 1-4
In this case, there is requirement of law firm to recover lost data from disk. Before this project I was unaware of anything which could help me in retrieving the deleted files. Before this project, I was not aware of the tool which could help in recovering the deleted files.
This project helped me to learn how to perform extraction on a disk. There, there are list of 5 steps:
1.Software used: I learnt about the various recovery tools. Taking care of the specifications and other things, ProDiscover basic was best among them. ProDiscover is the most budgeted and simple hand used forensic tool without much complications
2.Creating new project: I got to learn how to create a new project in ProDiscover basic and save it with name C1PRJ04.
3.Add image file: I came across how to add image file. Click on the Add from menu and then click on image file C1PRJ04.eve and open it. Check yes on the auto image checksum.
4.Adding pathname: I learned how to add pathname contusing the file. Expand the tree view and then content view and click the path name containing the disk. Analyse all the files displayed in the work area.
5.Sorting deleted files: I learned how to sort all the files into yes or no in the delete column header. This will display all the files in a sorted way.
6.Recovery from disk:I learn how to extract the deleted files by selecting the files with no in delete column header and pasting the files in the work area. This is done one by one, ProDiscover basic does not allow for multiple selections.
7.Save project: I learned that ProDiscover basic does not have auto save options, There is need to save the project manually. Always remember to exit the previous project before starting a new project.
Hands-On Project 1-5
This project is a continuous project from previous project. These hands on project help me in listing all the unallocated files/deleted from the disk. This learning will help me in undergoing my further academic studies.
Things which I learnt in carrying out this project:
Prodiscover Basic Download
1.Open up the project which has been saved in Hands-on-project 1-4 and open it.4 and open it.
2.There is need to sort all the unallocated and allocated files. This will help in creating listing of all unallocated files/deleted files. Sorting can be done by clicking on delete column header.
3.Select the files which have been marked as “yes” in delete column header. Mark the check box which is on left pane. A comment dialog will appear. This comment dialog box will help in adding description.
4.In the comment dialog box, I learnt to give a specific, meaningful description which can be identified later. Giving any random description might result in unidentified selected file from a list.
5. I came to know that the report of selected can be produced by clicking on the report in the tree view. This will help in checking all the selected files.
6.This Report can be exported. There is just need to click on the export button which given in the toolbar. I have given a specific name to this report for its identification C1PRJ05Report.
7. The most important task is to save the project. ProDiscover does not auto save things, these needs to be done manually.
8.Followed by this important learning, I come to know that no new project can be before exiting the previously started project. I save the project and exit the ProDiscover basic.
Task 2
Steps carried out in this project
This task consists of M-57 hypothetical case for the practical knowledge of new investigators. This project I need to identify whether terry is doing something against the policy of company or not.
The evidence is validated using OSForensics tool. Steps followed while carrying out the project:
1.Install the step and run the step and click on the “continue using free version”.
Figure 1: Running the software
2.Click on create new case.
Figure 2: creating new case
3.Fill up the given fields and browse for the desired location and select investigate disks from another machine and selects custom location and click on ok button.
Figure 3: saving new project part 1
Figure 4: saving new project part 2
4.Select the add device button and add the image file Terry-work-usb-2009-12-11.E01 and leave the default settings untouched. Select the image file and click on the open button.
Figure 5: file system browser
5.Click on the file search icon and following given window displays. Search for the keyword .following snapshot displays the result.
Figure 6: Keyword search
6.Now click on the create index icon and click on the predetermined file types and check the entire given file types under predetermined files and click on next button.
Figure 7: Creating index
7.In step 3 of 5 click on start indexing.
Figure 8: Start indexing
8.This indexing will take ETA of 1 hour to get complete. After indexing gets completed, click on open log to check errors while indexing and then select on manage case.
Figure 9: files getting indexed
Prodiscover Basic Forensics Software
9.Manage all the files which are considered in the operational image file.
Prodiscover Basic Free
Figure 10: examine the files
Examining the files inside the image file
By examining the terry-work-USB-2009-12-11.E01, I deduced that image file contains python files and 2 executable files and text documents. The image file contains .jpg format files in which contact details of a person is given.
Figure 11: .jpg format image
This image contains some critical text documents like patentterms.txt, urlscoprights.txt, urlspatents.txt. This file gives a clear indication that Terry is doing illicit or doing working against company’s policy.
Figure 12: text files and python files
Task 3
Fraud cases bring about new challenges every time than any other cases to the investigators. There are sequences of steps which I will preferably follow in investigating any potential fraud case.
Initial analysis:The process will start with asking the some basic Question and doing initial analysis what kind of fraud is that like is this is an identity or government theft, when did it occur, did it occur somewhere in other places.
Planning of investigation:
It is most critical part to investigate any potential fraud cases. The process will be in progress by identifying the chronological events which will help in giving follow up towards the actual case.
Victim’s interview:I will make every possible effort to get to know the victim. Basic questioning will be done with victim at some silent place. Every minute detail is very important in any fraud investigation; I will go with granular questions like where, what, when. I will conduct this interview for 2-3 times to make sure that all the instances of the investigation will be covered. Victim will be informed to take statements of their financial institutions on regular basis.
Securing evidences:Evidences, on whom support we build the events which may have occurred. I will make sure that I will maintain a copy of the bank accounts, emails, phone records or any social media posts. The evidences can be obtained electronically like Ms Word, MS access or hashes.These evidences need to be secured and validated. There are 4 major acquisition methods for storage devices:
1.Sparse
2.Bit-stream disk-to-disk
3.Bit-stream disk-to-image file
4.Logical
I will prefer Bit-stream disk-to-image file for validation process. This is the most common method adopted. It will produce replication of original drive bit-by-bit. I will prefer ProDiscover basic tool for carrying out the validation over storage media like USB drive or external drives.
I would choose hash algorithm such as “SHA1” over “MD5” because MD5 is broken and a lot of collisions come across MD5. SHA1 is more robust than MD5. MD5 is considered to be less preferred when the discussion comes to security applications.
References
1.Reynolds, M(2018). 7 Steps to Forensic Investigation Success Sedgwick. Retrieved from https://www.sedgwick.com/blog/2016/06/03/seven-steps-forensic-investigation-success.
2.Schiro, G. (2018). Collection and Preservation of Evidence. Retrieved from http://www.crime-scene-investigator.net/evidenc3.html.
3.Team, T. (2018). All you want to know about Digital Evidence. Retrieved from https://taxguru.in/income-tax/cbdt-releases-digital-evidence-investigation-manual.html.